|
Rescooped by THE OFFICIAL ANDREASCY from Cybersecurity Leadership |
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
No comment yet.
Sign up to comment

Gust MEES's curator insight,
March 8, 2022 7:20 AM
Google is buying cybersecurity company Mandiant in an all-cash transaction valued at approximately $5.4 billion.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/21st-century-innovative-technologies-and-developments/?&tag=Acquisitions
Russell Roberts's curator insight,
February 22, 2022 10:58 PM
A helpful guide to protecting your business and personal data.

Gust MEES's curator insight,
March 30, 2016 5:34 PM
Introducing the 'Treacherous 12,' the top security threats organizations face when using cloud services
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cloud-Security

Carina Bethea's curator insight,
June 14, 2015 4:45 PM
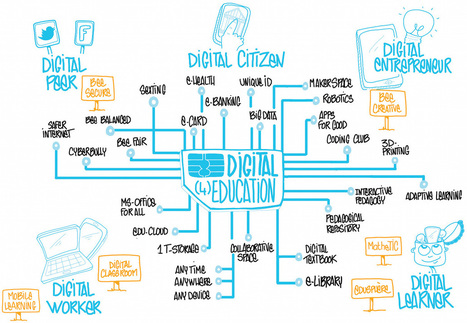
This graphic is so unique and informative. The "digital learner" section on the bottom right especially is a great visual summary of many of the other articles. It includes "adaptive learning", "eLibraries" and "digital textbooks", which are all topics that have been mentioned in other articles. Some points, like "3D Printing", add another layer of possibilities. What strikes me most about this is how the different fields flow together. It is a convergence of media, education and the work world, which makes a lot of sense. Just like the internet, everything is connected. It seems to be the top goal to become a literate "digital citizen" in the future...

Gust MEES's curator insight,
February 9, 2015 2:23 AM
The Federal Trade Commission (FTC) is aware we live in a connected world. Americans wear Fitbits, have Nest thermostats, use automated light systems from companies like Belkin and Philips, even have televisions that predict what they want to watch. But in a new report, the FTC has a warning: Existing privacy regulations don’t really cover the Internet of Things, and the Commission doesn’t really trust device manufacturers to do the right thing—or even be aware of the risks of collecting all that data. Learn more: - http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables - http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things - http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things 
deepak's curator insight,
February 9, 2015 3:08 AM
उत्तर प्रदेश और किसान : उत्तर प्रदेश राज्य के लिए राजनितिक सर्वे मे हमने पाया है कि अब तक उत्तर प्रदेश में ज्यादा विकास नही हो पाया है| जैसे: कृषि,शिक्षा,उधोग आदि क्षैत्र में| यह राज्य कृषि उत्पादन मे भारत मे सर्व श्रेठ है| यहाँ की भूमि बहुँत उपजाऊ है जिससे हमे बहुँत फसल प्राप्त होती है जैसे गैहू, धान ,सरसो ,दाले आदि| जिनहे हम विदेश में निर्यात करे तो अच्छा धन कमा सकते हैं पर इस राज्य में शासन करने वाले इसे कम कीमत पर खरीद कर अच्छी कीमत पर बेच देते है | लाभ राशि यहाँ के लोग नही बल्कि यहाँ की भ्रष्ट सरकार की साहयता से पूंजीपति उठा लेते है जिस्से किसान अच्छी कीमत नही कमा पाते है और किसान आर्थिक रूप से ग्रस्त होते जा रहे है उत्तर प्रदेश की इन सभी कमियो को मध्यनजर रखते हुए भारतीय जनता पार्टी विकास के लिए कुछ जरूरी कदम उठाएगी | 1. सभी किसानो के लिए कृषि धन योजना खाते खोले जाएँगे | जिससे वह गन्ना अदि फसल का भुगतान अपने खाते में पा सकते है | 2. किसानो के लिए लोन की सुविधा कम दर पर रखी जाएंगी | जिस्से वह ज्यादा समय में आसानी से चुका सके | 3. फसल के बारे मे शिक्षा प्रदान करने के लिए कृषि विशेषज्ञयो को भेजा जाय जाएंगा | 4. शिक्षा का स्तर बाल व बालिकाओ का निगमन साक्षरता की ओर होगा जिस्मे नए प्राइमरी व इंटर तक के स्कूल खोले जायंगे | 5. सभी व्यावसायिक को व्यवसाय प्रदान किये जायंगे वो भी एक अच्छी प्रति दिन कीमत पर | 6. उत्तर प्रदेश वासियों को कम यूनिट दर पर बिजली परदान की जाएगी | संजय सिंह जी को भारतीय जनता पार्टी दुआर जेवर छेत्र के लिए चुने गये है जो इस छेत्र मे काफी सुधार करने के इच्छुक है | 1. किसानो का गन्ना तथा आदि कृषि सम्बन्धी मुद्दा सुलझेंगे | 2. किसानो को आर्थिक सहायताए देंगे | 3. जेवर में सड़क सम्बन्धि तथा आदि कार्य कराएंगे | |

Gust MEES's curator insight,
April 27, 2022 7:36 AM
The multibillion dollar valued Bored Ape Yacht Club NFT project's Instagram account was hacked, resulting in the loss in millions of dollars worth of NFTs.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=blockchain
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=WEB3
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=NFT

Gust MEES's curator insight,
March 2, 2022 3:21 PM
The NATO Cyber Security Centre (NCSC) has completed its test run of secure communication flows that could withstand attackers using quantum computing.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/21st-century-innovative-technologies-and-developments/?&tag=Quantum-Computing

Gust MEES's curator insight,
December 13, 2021 6:09 PM
Cybersecurity experts believe CVE-2021-44228, a remote code execution flaw in Log4j, will take months, if not years, to address due its ubiquity and ease of exploitation.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Log4j

Andreas Christodoulou's curator insight,
July 5, 2017 11:39 PM
When it comes to business security and personal privacy, do not underestimate the importance of losing or corrupting data. SEE ALSO: How Big is your Digital Footprint? -> https://www.linkedin.com/pulse/20140706090838-57593230-how-big-is-your-digital-footprint Is Google Taking Over Our Daily Lives? -> https://www.linkedin.com/pulse/20140712100415-57593230-is-google-taking-over-our-lives

Gust MEES's curator insight,
October 1, 2015 1:03 PM
October is National Cyber Security Awareness Month in the United States. This year’s campaign emphasizes cybersecurity as part of a deliberate strategy and a shared responsibility, not just a checkbox item. Learn more: https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/ 
Wendy Zaruba's curator insight,
October 2, 2015 8:48 AM
October is National Cyber Security Awareness Month in the US. Great article, what do you know or what part do you play in Cyber Security?

Gust MEES's curator insight,
March 12, 2015 12:15 AM
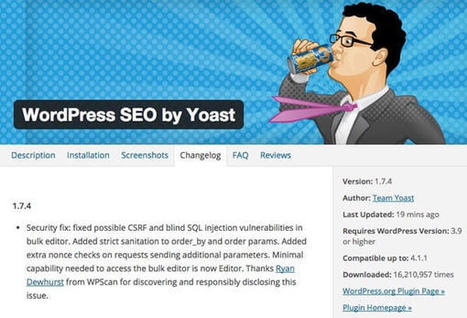
A serious vulnerability was found in one of the most popular WordPress plugins, and guess what? It got fixed really quickly. :) All that remains is for you to apply the update on your web server. |