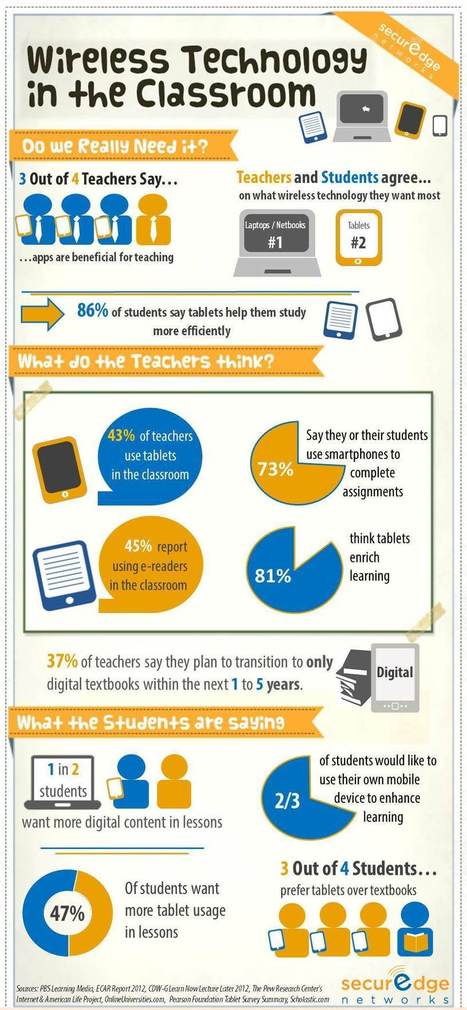
Today’s education system is evolving to take full advantage of the potential of mobile technology devices to inspire learning and create independent, critical thinkers.
However, with tight budgets, many schools are hoping to bring technology into the classroom without the costly burden of purchasing a device for each student. One potential solution that is being explored is BYOD, or Bring Your Own Device. This allows students to bring their personal laptops, tablets, and smartphones from home and use them for educational applications in the classroom.
At a time when budgets are shrinking, school districts are considering BYOD programs to integrate cost-effective technology into their educational programs. It’s a promising idea, especially for schools that lack sufficient technology budgets. BYOD takes advantage of the technology that students already own and are familiar with.
However, BYOD programs have been met with some criticism from staff and administrators who believe the challenges outweigh the perceived benefits. Continue reading...



 Your new post is loading...
Your new post is loading...

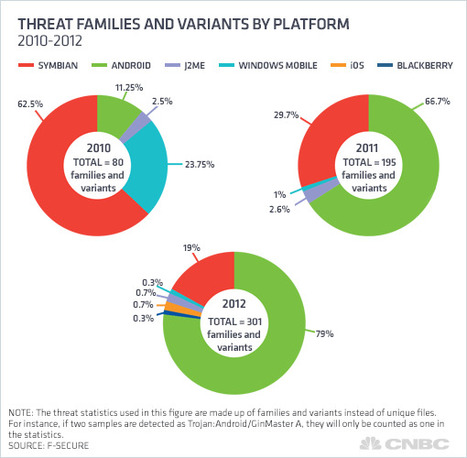





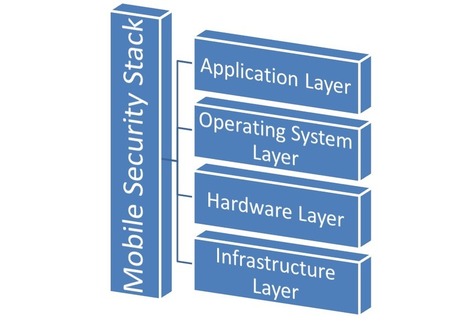
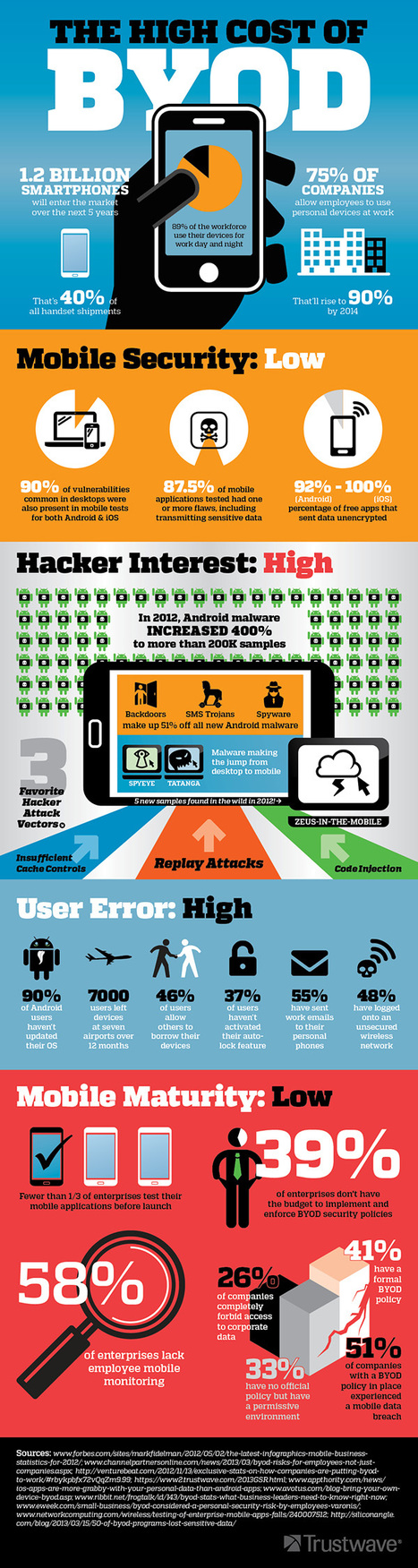
![Survey: Despite Security Incidents, BYOD Worth The Risks [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/AmjfVVh3JSRFrcTVEXBUozl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)




![Adoption Rates of New Styles of K-12 Teaching [Infographic] - BYOD | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/7CwBx2opz0RQK34FnQvyPDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



![A Glimpse At The BYOD Device Of The Future [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/-dyQ6CXOo2PTse-Jll5ofDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
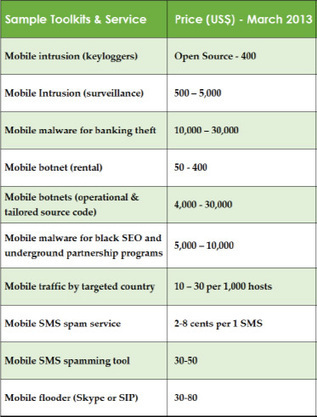
![Mobile Security – Android vs. iOS [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/SyLGbWn__SYdkCXNd6mDEDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

![The Importance Of Mobile Learning In (And Out Of) The Classroom [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/an8zp0xrd2ueChG43lwYQTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

![BYOD: Mobility making it easier for insiders to take IP [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/7qGVluSAqAo_xdmrGdGXozl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free/?tag=Mobile-Security
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Mobile+Security