Summer 2013 App Reputation Report to examine the hidden behaviors behind free and paid mobile apps
The cloud-based, fully automated Appthority App Risk Management Service performed static, dynamic and behavioral app analysis on the 400 most popular free and paid apps on the iOS and Android platforms.
Appthority analyzed each app for particular behaviors within a test environment
.
Highlights from the App Reputation Report are:
- Overall, 83% of the most popular apps are associated with security risks and privacy issues.
- iOS apps exhibited more risky behaviors than Android apps. 91% of iOS apps exhibit at least one risky behavior, as compared to 80% of Android apps.
- 95% of the top free apps and 77.5% of the top paid apps exhibited at least one risky behavior.
- 78% of the most popular free Android apps identify the user's ID (UDID).
- Even though Apple prohibits its developers from accessing the UDID, 5.5% of the tested iOS apps still do.
- 72% of the top free apps track for the user's location, compared to 41% of paid apps.
- Although paid apps already generate revenue when downloaded, 59% of paid iOS and 24% of paid Android apps still support in-app purchasing.
- Furthermore, 39% of paid iOS and 16% of paid Android apps still share data with ad networks.



 Your new post is loading...
Your new post is loading...








![Building a successful BYOD program-Education [pdf] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/-iSYiJBy7cQ3wAU3f-jM4jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

![Going BYOD [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/Ch1oqxgT1jQ06m3I7BtCdDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



![The Past, Present, And Potentially Amazing Future Of Smartphones [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/XLeqfcxNUkKt4m7JWdDZtjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

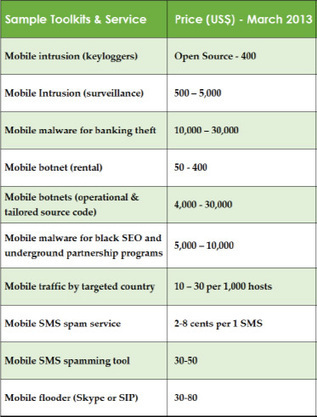





![BYOD: The Good, The Bad and the Ugly [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/vP-iurN-SzKBXJzm0u8Qtjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![Mobile Threat in Action [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/cJttrx6XoZpu_ERcpy9jUjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![BYOD: Bring Your Own Risk (BYOR) [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/y5NTg9uYlSpK6x67Mbb7WDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
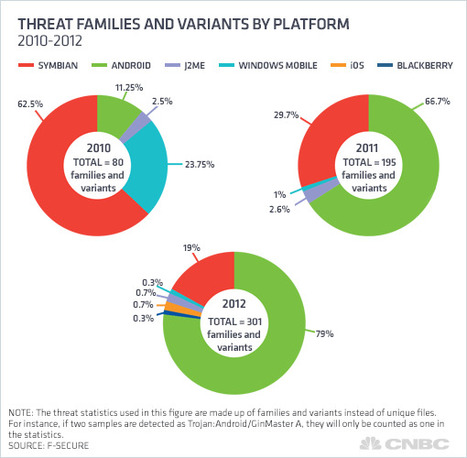







Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
Learn more:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security