Ein deutscher Online-Shop hat einen generalüberholten Router verkauft, der zuvor offenbar für Google Dienst schob. Das Gerät hat den Internetriesen mit allerhand sensiblen Informationen verlassen, welche die neuen Besitzer problemlos auslesen konnten.
Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/2012/11/05/naivety-in-the-digital-age/



 Your new post is loading...
Your new post is loading...



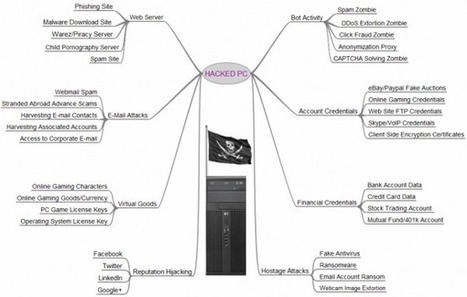





Learn more / En savoir plus / Mehr erfahren:
https://gustmees.wordpress.com/2012/11/05/naivety-in-the-digital-age/