Why (And How) Teachers Should Start Learning and Teaching Cyber-Security . What should get be taught and learned more in the 21st Century while using ICT?
In the 21st Century, Education has a BIG responsibility to adapt to the very quick change in the world and to teach the students the knowledge they need and which are required to fulfill the market’s needs!
The market’s needs are ALSO to employ people with the basics of Cyber-Security knowledge as a modern company needs to protect its online reputation and a data loss could be lethal to them, their ruin eventually! SO, the new employees is the students coming out of school, College, High school, Universities; ALL of them need to have the basic knowledge of Cyber-Security to be competitive in a working market where there is more and more unemployment worldwide…
===> A company would take advantage of a new employee who as already the necessary knowledge of Cyber-Security as the company doesn’t need to train him, which saves it a lot of money! <===



 Your new post is loading...
Your new post is loading...






![Keep Your Pesky Hands Off my Mobile Data! [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/IVbwKIbFUxnPBlG4x_kuWTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![Managing Mobile Privacy | Security Intelligence Blog [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/m8EBNAOuN5Zr7PdORj8fTDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)











![Why You Should Care About Mobile Security [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

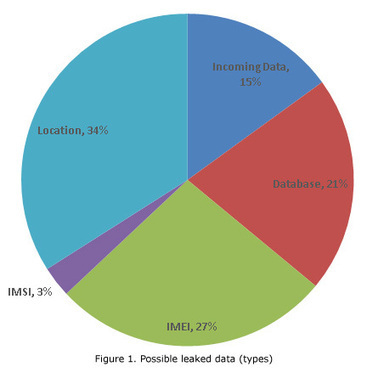
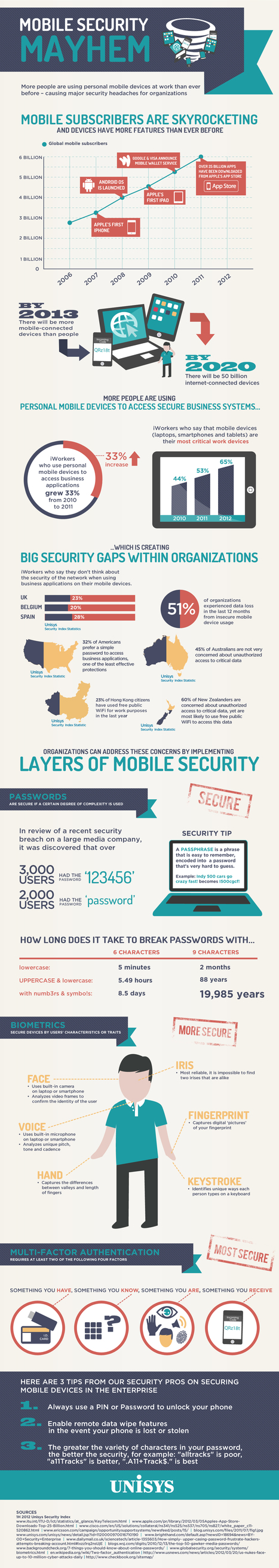





Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Competency-based+Learning
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Competency