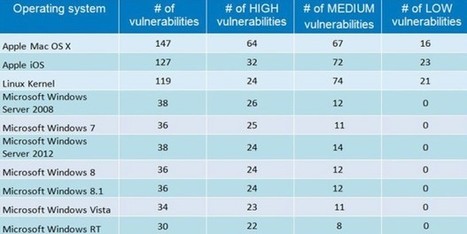
Les contrôles d’accès censés protéger les données personnelles comme le carnet d’adresses peuvent être contournés, comme vient de le démontrer un chercheur en sécurité.
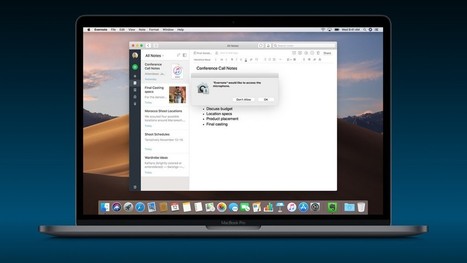
Depuis hier, 24 septembre, les utilisateurs d’ordinateurs Mac peuvent installer la dernière version du système d’exploitation macOS Mojave. Malheureusement, celle-ci est déjà impacté par une importante faille de sécurité qui met à mal la protection des données personnelles. Avec macOS Mojave, Apple a en effet musclé les contrôles d’accès aux fichiers et aux applications sensibles tels que le carnet d’adresses, l’historique des messages, la base de données d’email, le microphone, la caméra, etc. Mais ces contrôles d’accès peuvent être court-circuités, comme le démontre le chercheur en sécurité Patrick Wardle.
Cet expert a développé une application baptisée « breakMojave » capable de siphonner en douce le carnet d’adresses de l’utilisateur sans rien lui demander. Il a montré le déroulement du hack dans une vidéo Vimeo. Au départ, on constate qu’aucune application tierce n’a accès au carnet d’adresses. Le chercheur ouvre ensuite une fenêtre Terminal et tente d’accéder directement aux données du carnet d’adresses, sans succès. Le lancement de breakMojave provoque enfin l’extraction des données, qui se retrouvent copiées en vrac sur le bureau.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security



 Your new post is loading...
Your new post is loading...









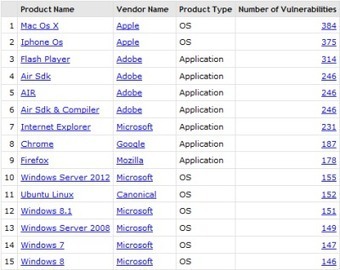

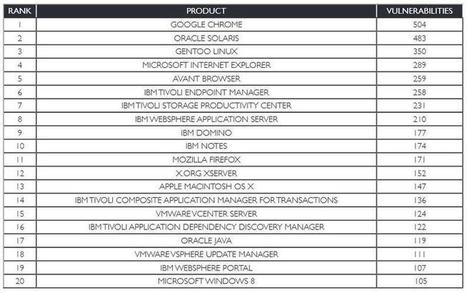
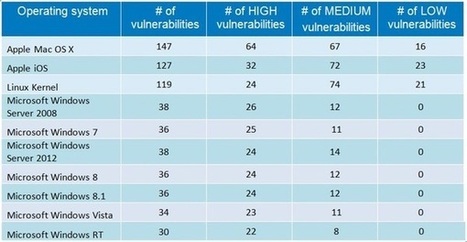







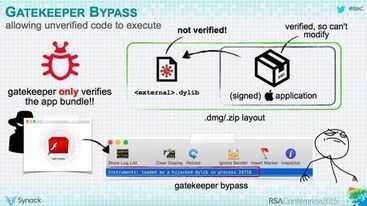
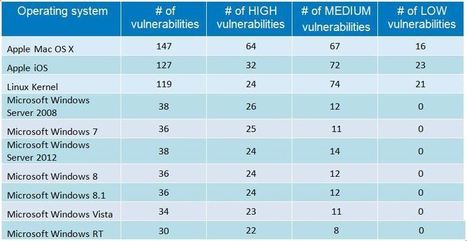





Let us talk about Hygiene... Strange, I make an introduction about Hygiene in an Cyber-Security Blog, ISN'T it?!! Well, there is a reason behind: WHEN WE use a computer, Smartphone and/or any OTHER technical device (such as cars as well...) WE need to take care of them! AND our body? The same: WE…
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/21st-century-learning-and-teaching/?&tag=Cyber-Hygiene
https://www.scoop.it/topic/securite-pc-et-internet
https://www.scoop.it/topic/apple-mac-ios4-ipad-iphone-and-in-security
https://gustmees.wordpress.com/2017/10/26/critical-thinking-and-proactive-thinking-a-must-in-modern-edu/