 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
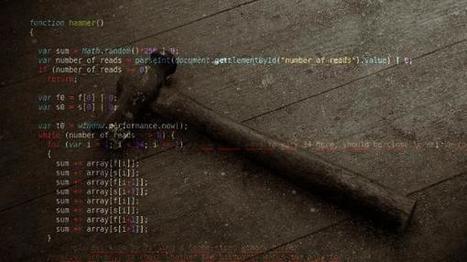
Beim Rowhammer-Angriff klöppelt der Angreifer so lange auf einem Speicherbereich rum, bis benachbarte Bits flippen. So kann man Systeme lahmlegen und sich sogar Admin-Rechte verschaffen. Unglaublicherweise klappt das auch mit JavaScript über das Internet.
Im März schlug die Veröffentlichung einer Reihe von Google-Forscher große Wellen: Auf DRAM-Chips lassen sich mit Gewalt Bits flippen und Angreifer können so den Rechner des Opfers abstürzen lassen oder gar Admin-Rechte erlangen. Jetzt haben Forscher der Technischen Universität Graz und der Firma Technicolor es geschafft,den sogenannten Rowhammer-Angriff auf JavaScript zu übertragen.
Damit kann man den Speicher aus der Ferne malträtieren, wenn das Opfer eine präparierte Webseite besucht. Die Gefahr eines gezielten Angriffs im Alltag ist zwar nach wie vor begrenzt, wenn es dem Angreifer aber nur darum geht, Daten in den Systemen zu verfälschen oder diese zum Absturz zu bringen, so ist dem Tür und Tor geöffnet und zwar nicht etwa nur für x86, sondern prinzipiell auch für ARM und andere Architekturen.
Mehr erfahren / Learn more:
https://gustmees.wordpress.com/2014/08/24/coding-a-new-trend-in-education-and-a-big-responsibility/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Der sorglose Umgang der Mitarbeiter mit mobiler Technologie gehört laut IDC neben Malware und Phishing-Attacken zu den häufigsten Risiken beim Thema Mobile Security in Unternehmen.
Zu den größten Sicherheitsrisiken aus Sicht der IT-Verantwortlichen zählen dabei Mobile Malware mit 42 Prozent, gefolgt von Phishing und Social Engineering mit 35 Prozent. Weitere 30 Prozent gaben an, dass das Fehlverhalten von Anwendern – vorsätzlich oder unabsichtlich – ein großes Risiko darstelle. Sie planen deshalb, die Mitarbeiter stärker für das Thema Mobile Security zu sensibilisieren. Dies soll vor allem durch Trainings der Anwender und IT-Mitarbeiter sowie Richtlinien zur sicheren Nutzung mobiler Endgeräte geschehen - wobei hier die Wünsche der IT-Verantwortlichen und der User teils sehr unterschiedlich sind. . Learn more / Mehr erfahren: . .

|
Scooped by
Gust MEES
|
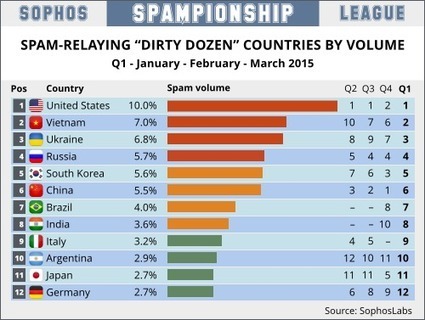
Here they are: the latest "Dirty Dozen" SPAMPIONSHIP tables, detailing the globe's most dastardly distributors of delinquent data during the first quarter of 2015.
If you haven't seen the Dirty Dozen before, here's how it works.
SophosLabs maintains a large network of spamtraps, operated around the world with the express purpose of collecting spam.
And, boy, do they collect spam!
Of course, whenever spam falls into a trap, we can tell where the final step of its journey started by looking at the IP address of the computer from which the offending email was sent.
It's possible to track back individual IP numbers fairly accurately, sometimes down to a street block, often to a suburb or metro area, and almost always to the sender's country.
In other words, our spamtraps tell us which countries are the worst senders of spam.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Spam
- https://gustmeesen.wordpress.com/2012/01/07/pc-security-howto-fight-spam-efficiently/

|
Scooped by
Gust MEES
|
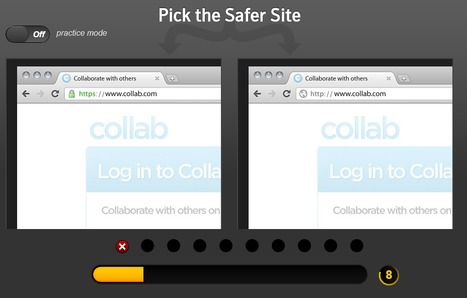
Can you tell the difference between a real site and a fake one?
Do you know how to stay safe online?

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
HTTP Strict Transport Security (HSTS) is supposed to keep you more secure online, but it could be used to track you against your will.
Mark Stockley explains...

|
Scooped by
Gust MEES
|
OPSWAT’s latest market share report ranks Avast as the top vendor and finds that 90% of devices haven’t updated their antivirus definitions in the last seven days.

|
Scooped by
Gust MEES
|
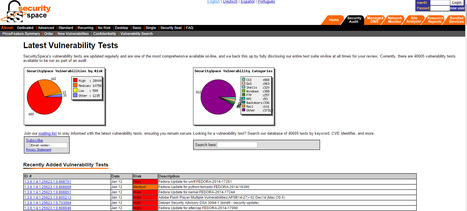
SecuritySpace offers free and fee based security audits and network vulnerability assessments using award winning scanning software.

|
Scooped by
Gust MEES
|
Online security companies have been making their predictions for 2015, from the malware that will be trying to weasel its way onto our computers and smartphones to the prospect of cyberwar involving state-sponsored hackers.
Here’s a summary of what you should be watching out for online in 2015, based on the predictions of companies including BitDefender, KPMG, AdaptiveMobile, Trend Micro, BAE Systems, WebSense, InfoSec Institute, Symantec, Kaspersky, Proofpoint and Sophos. The links lead to their full predictions.
Read more: http://uk.businessinsider.com/beyond-phishing-experts-predict-the-cybercrime-of-2015-2014-12?utm_content=bufferbd004&utm_medium=social&utm_source=twitter.com&utm_campaign=buffer?r=US#ixzz3N3npIVff
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Protect yourself from rogue DNS servers. FREE online Router-Security-Checker.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
The way Eugene Kaspersky sees it, there may soon come a day when you wake up and your coffeemaker refuses to brew anything – or worse, will only brew decaf – until you pay up on the ransomware that has infected it.
Kaspersky, CEO of Kaspersky Lab, told some of the company’s top partners at its annual North American Partner Conference here this weekend that he believes IoT stands not only for “Internet of Things,” but also for “Internet of Threats.” The emergence of IP and intelligence in an increasing number of previously disconnected devices will lead to new and novel attack vectors, the executive predicted.
“It’s not just the pleasures of this world, the benefits and the beauty, that we have to think about,” Kaspersky told partners. “We also have to think about the other side, the bad guys, as well.”
And while the coffee maker was a bit of a perhaps a tongue-in-cheek example, Kaspersky said he does see a variety of attack opportunities on devices that have heretofore not been connected to the network. The first one to be hit, he posited, will be right in our living rooms.
Mehr erfahren / Learn more / En savoir plus:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/

|
Scooped by
Gust MEES
|
Adobe has released Flash Player 16.0.0.305, a new version that fixes the latest zero-day flaw (CVE-2015-0313) that is currently exploited in...

|
Scooped by
Gust MEES
|
Scannen Sie QR-Codes überall von unterwegs aus und öffnen Sie Texte, Bilder, Websites etc. ohne Angst vor mobilen Bedrohungen. GRATIS.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Im Jahr 2014 blockierten die Lösungen von Kaspersky Lab insgesamt 3.693.936 Infektionsversuche unter Mac OS X. Die Experten von Kaspersky Lab entdeckten 1.499 neue Schadprogramme für Mac OS X, das sind 200 Schädlinge weniger als im entsprechenden Vorjahreszeitraum.
===> Jeder zweite Anwender von Apple-Produkten war einem Angriff ausgesetzt. <===
Im Laufe des Jahres war jeder Mac-OS-X-User durchschnittlich neunmal mit einer Cyberbedrohung für sein Betriebssystem konfrontiert.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
|



 Your new post is loading...
Your new post is loading...
























You may want to think twice before you install that security camera.
Mehr erfahren / En savoir plus / Learn more:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cars