 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Eine Auswertung der CVE-Liste zeigt, für welche Programme und Betriebssysteme 2015 die meisten Sicherheitslücken gemeldet wurden. Wie sicher die Software ist, lässt sich daraus jedoch nicht ableiten.
Auf der wichtigsten Liste öffentlich bekannter Sicherheitslücken tauchten im Jahr 2015 besonders häufig Mac OS X, iOS und Flash auf. Das geht aus einer Auswertung von CVEDetails.com hervor, die auf der CVE-Liste (Common Vulnerabilities and Exposures) basiert.
Im Rahmen des CVE-Projektes vergeben wichtige Software-Hersteller wie Apple, Adobe, Microsoft und Mozilla eindeutige IDs für Sicherheitslücken, in Zusammenarbeit mit der Non-Profit-Organisation Mitre.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
CyberHygiene For Beginners, Easy To follow Steps For Anyone | Reflexes To Get Used To . Internet safety is the responsibility of EVERYONE! It isn't actually THAT difficult to apply a healthy behavior on the internet to stay secure, one needs to have some reflexes, daily reflexes... Let us call them CyberHygiene…

|
Scooped by
Gust MEES
|
Selon gizmag, nos chères têtes blondes s’attendent aujourd’hui à ce que les jouets offerts puissent se connecter à Internet et être couplés à des appareils intelligents, leur permettant ainsi d’accéder aux dernières tendances technologiques en date, parfois même avant leurs parents. Toutefois, chers parents, bien que nous ne puissions que vous recommander de réfléchir à deux fois avant d’acheter à vos enfants un jouet connecté, soyez vous aussi vigilants car, comme vous pourrez le lire ci-dessous, les risques de sécurité ne concernent pas uniquement les gadgets pour enfants.
L’Internet des objets (IdO) devient rapidement partie intégrante de notre réalité car un plus grand nombre de nos objets du quotidien renferment maintenant de l’électronique, des logiciels, des capteurs ou sont capables de se connecter au réseau, leur permettant ainsi de recueillir et d’échanger des données. Combien de ces objets, pensez-vous alors, peuvent se transformer en vrais chevaux de Troie ? La guerre de Troie prit fin quand les Grecs firent preuve de malice pour entrer dans la ville de Troie, cachant des soldats dans un énorme cheval de bois. Les Grecs firent semblant d’embarquer sur leurs navires et de prendre le large tandis que les Troyens, peu méfiants, s’emparaient du cheval en signe de victoire, le faisant entrer dans la ville. Plus tard cette nuit-là, les Grecs sortirent tant bien que mal dudit cheval de bois et ouvrirent les portes de la ville au reste de l’armée grecque afin que cette dernière pénètre dans la ville et la détruise. Quels attaquants peuvent potentiellement surgir de vos cadeaux de Noël ?
Learn more / En savoir plus / Mehr erfahren:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=wearables
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
- http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/

|
Scooped by
Gust MEES
|
A new form of attack has brought a long-standing criminal malware suite to an NSA level of sophistication.
A newly revealed malware that has been in use since at least the beginning of this year has been dubbed a “bootkit,” for its ability to infect a computer at the most fundamental level, running when the computer boots to actually load before the operating system itself. It’s part of the widespread “Nemesis” malware suite, and while it is currently aimed at financial institutions, the inclusion of bootkit functionality in a relatively “mass market” solution means the powerful form of cyber infiltration is coming to a much wider array of victims. The issue is that since a bootkit can load in malware programs before Windows itself loads, Windows processes have a hard time identifying malicious activity, and an even harder time removing it. Completely reinstalling the OS won’t do it — this is rather like the NSA attacks that can resist even a total format of the drive, but so far as we know those mostly at least require hardware infiltration of the target. In this case, this purely software virus can install itself behind your computers eyes, and thus never be seen.

|
Scooped by
Gust MEES
|
ENISA rolls out a continuation to its most used and valued technical training material, on Mobile Threats Incident Handling and Artefact analysis The material released is two-fold: - The new content familiarises trainees with concepts, tools, and techniques used for incident handling on mobile devices, and offers a methodology on how to react - properly and timely - when the necessity comes.
- The new artefact analysis training material helps information security analysts to correctly analyse malware and understand its potential functionality, enabling the organisation to create proper countermeasures and mitigation plans.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Für die fünfte Edition der Seniorenmesse Top50+ hatten sich wieder viele Senioren am 03. und 04. Oktober im Casino 2000 in Mondorf eingefunden. Reges Interesse fand die Live Hacking Demo on stage, die von Michael Hamm, Sicherheitsexperte bei CIRCL- Computer Incident Response Center Luxembourg, durchgeführt wurde. Anhand von konkreten Beispielen demonstrierte er, wie Cyberkriminelle vorgehen um Passwörter knacken.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A new evil vulnerability affecting the AirDrop service could be exploited by attackers to silently infect iPhones and Apple Macs. Versions prior to the latest Apple OS version, the newborn iOS 9, are affected by a serious AirDrop Bug. The AirDrop Bug could be exploited by hackers to take full control of Apple iPhone or Mac machines. The AirDrop Bug has been disclosed by the Australian security researcher Mark Dowd, AirDrop is a proprietary service that enables the transfer of documents among supported Macintosh computers and iOS devices.
Learn more:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Christian Fredrikson (CEO des Sicherheitsanbieters F-Secure) verrät im exklusiven Interview die drei größten Sicherheitslücken in deutschen Unternehmen
Mehr erfahren / En savoir plus / Learn more:
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
According to gizmag, today’s kids expect their toys to connect to the internet, pair with smart devices, and let them join in the latest tech trends, often before their parents. However, while there are good reasons parents should think twice before buying tech toys for their kids, as you will read below, security risks aren’t just confined to gadgets for children.
As the concept of the Internet of Things (IoT) rapidly becomes reality as more and more objects are embedded with electronics, software, sensors and network connectivity that enables them to collect and exchange data, how many of your Christmas gifts could be the equivalent of the Trojan Horse? It was a decisive end to the Trojan War when the Greeks used subterfuge to enter the city of Troy, hiding some of their army inside a huge wooden horse. After pretending to sail away, the unsuspecting Trojans pulled the horse into their city as a victory trophy. Later that night the Greek force crept out of the horse and opened the city gates for the rest of the Greek army to enter and destroy the city. What attackers could be potentially unleashed in your Christmas gifts?
Learn more:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
https://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/

|
Scooped by
Gust MEES
|
Negotiators of the European Parliament, the Council and the Commission have agreed on the first EU-wide legislation on cybersecurity.
Information systems – computing resources such as networks and databases that enable essential services, businesses and the internet to function – are affected by an increasing number of security incidents. These incidents can have different origins, including technical failures, unintentional mistakes, natural disasters or malicious attacks. They could disrupt the supply of essential services we take for granted such as electricity, water, healthcare, or transport services.
It is a priority for the Commission to help prevent these incidents, and in case they occur, provide the most efficient response. This is why the Commission put forward in 2013 a proposal for a Directive to ensure a high common level of network and information security (NIS) in the EU. The European Parliament and the Luxembourg Presidency of the EU Council of Ministers last night reached an agreement on the rules which will:
improve cybersecurity capabilities in Member States
improve Member States' cooperation on cybersecurity
require operators of essential services in the energy, transport, banking and healthcare sectors, and providers of key digital services like search engines and cloud computing, to take appropriate security measures and report incidents to the national authorities

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
We’re at the Wild West stage of the Internet: the pioneers have come and gone, the big operators are building their mines and ranches, and now comes the plague of carpetbaggers. Just as children once grew up surrounded by guns, but somehow managed to survive, our children now are growing up in the mine-strewn trench warfare landscape of the Internet. It can in fact be navigated with some degree of safety, but not by the incautious.
It falls to us – whether we are teachers, parents or security engineers – to bring up the next generation with some hope of survival. The challenge is to simultaneously encourage exploration and enforce security, or if that’s not available, at least some degree of safety. Our culture weathered the frontier era more or less successfully, so I’m inclined to believe we can deal with the threats of the Internet. The challenge is to do it with minimal damage.
Learn more:
https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
https://gustmees.wordpress.com/2012/11/29/cyber-hygiene-ict-hygiene-for-population-education-and-business/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Vint Cerf is known as a "father of the Internet," and like any good parent, he worries about his offspring -- most recently, the IoT.
"Sometimes I'm terrified by it," he said in a news briefing Monday at the Heidelberg Laureate Forum in Germany. "It's a combination of appliances and software, and I'm always nervous about software -- software has bugs."
The Internet of Things will offer the ability to manage many of the appliances we depend on, acknowledged Cerf, who won the Turing Award in 2004. With its ability to continuously monitor such devices, it also promises new insight into our use of resources, he said.
Devices such as Google's Nest thermostat, for instance, can "help me decide how well or poorly I've chosen my lifestyle to minimize cost and my use of resources -- it can be an important tool," he said.
As with so many technological tools, however, there are plenty of potential downsides. Safety is one of them.
Cerf is now vice president and chief Internet evangelist at Google, but you won't find him enjoying any of the massage chairs the company provides for its employees. "I know they're run by software -- I worry they will fold up on me," he quipped.
As more such appliances are run by software, people will be increasingly reliant on programmers' ability to write good code, he pointed out.
"It's fraught with issues, some technical and some legislative," he said. "Who is liable when an appliance doesn't work the way it should, and what if that's a software question?"
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Internet+of+Things
http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things
http://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cars
|



 Your new post is loading...
Your new post is loading...

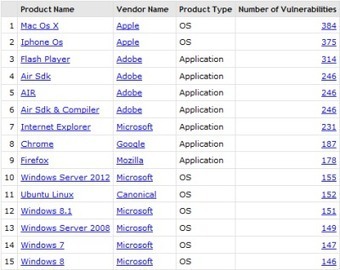













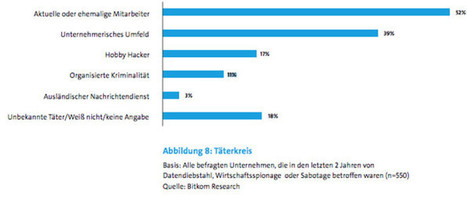
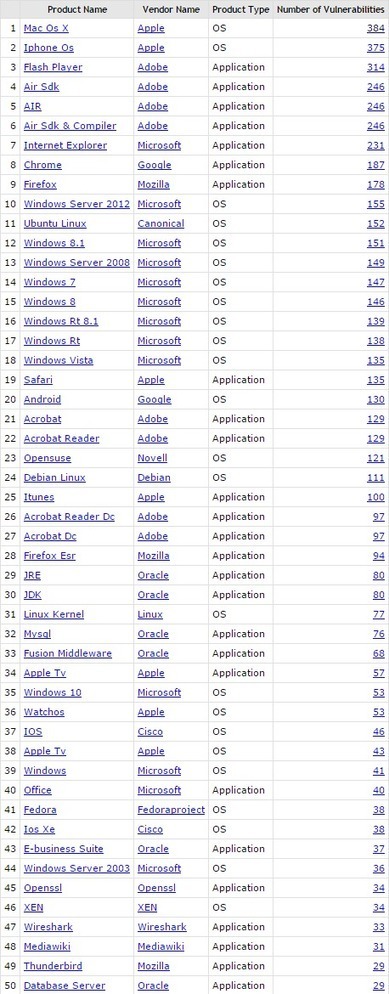




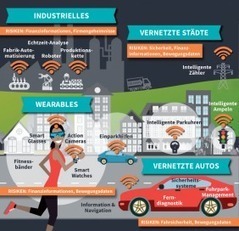












Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/securite-pc-et-internet