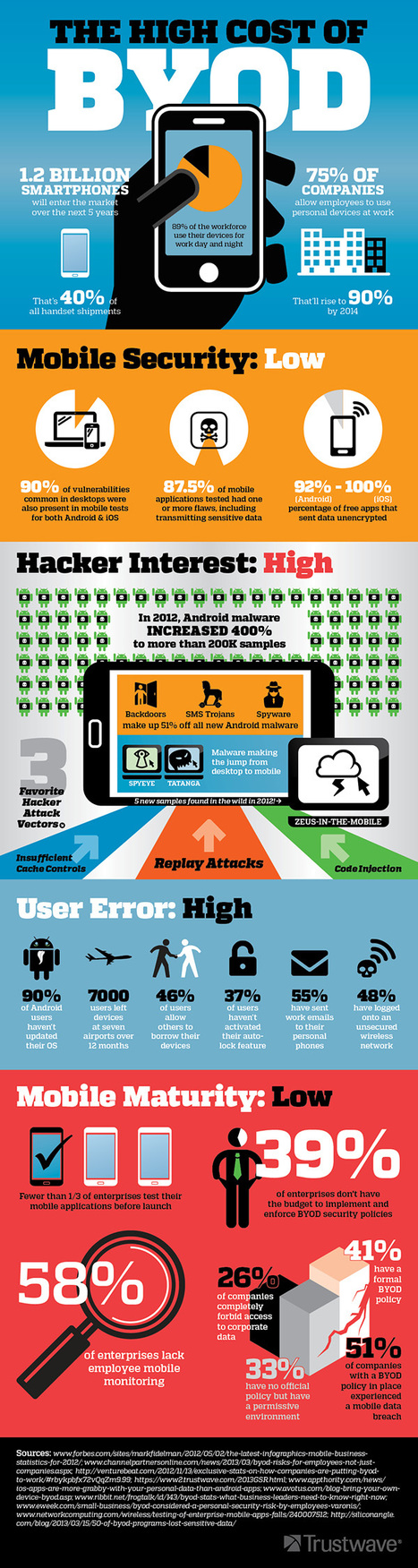
Businesses today are embracing BYOD- 75% of businesses let employees use their own devices to access the network. What threats are lurking behind this mobile revolution?
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Current selected tag: 'BYOD Policy'. Clear
The enterprise is increasingly turning to mobile app developers for solutions to leverage interest in BYOD. Gartner estimates that 70% of mobile professionals will conduct their work on personal smart devices by 2018.
As developers create apps to run on multiple platforms and plug into existing ERPsystems, vulnerabilities grow. From insecure data storage to improper session handling, from side channel data leakage to weak server-side controls, there are many risks to consider and robust penetration testing is an absolute must. Via Frederic GOUTH
Gust MEES's insight:
As developers create apps to run on multiple platforms and plug into existing ERPsystems, vulnerabilities grow. From insecure data storage to improper session handling, from side channel data leakage to weak server-side controls, there are many risks to consider and robust penetration testing is an absolute must. Check also: - http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free?tag=Mobile-Security - https://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
The Bring Your Own Device phenomenon is reshaping the way IT is purchased, managed, delivered, and secured. Our editors and analysts will delve into what it means, the key products involved, how to handle it, and where it’s going in the future.
Gust MEES's insight:
Lots of videos from THE experts, a MUST check out!!!
Check also:
- https://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
The 'bring your own device' phenomenon is reshaping the way IT is purchased, managed, delivered, and secured. This ebook rounds up our best BYOD content and puts it all into a convenient PDF.
Gust MEES's insight:
A new survey has found rising interest in mobile device management platforms to address mobile security threats. Still, few IT professionals indicate a real deployment of the platforms.
The survey found that 34 percent of respondents considered mobile devices a serious threat to business, and 55 percent said they were thinking more about the security of corporate smartphones and tablets than they did last year. Despite the attention given to mobile malware and attacks targeting device owners, the biggest threat to enterprises are lost and stolen devices, according to most security experts.
===> The survey found that 10 percent of respondents experienced data leaks following the loss or theft of mobile devices. <===
Gust MEES's insight:
A MUST read!
Check also:
- https://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
An infographic from security-testing company Veracode explores the rise of data breaches and what it could mean for businesses and consumers.
The return of IM worms, such as the recent Skype threat, underscores a risk that IT managers face in an increasingly BYO world.
It was an early form of consumerization with people bringing the applications they used in their personal lives into the workplace. Call it a “BYOA” approach: Bring Your Own Application. Always being ready to adapt to emerging trends, attackers started crafting malware that would exploit the weaknesses these new applications introduced into the workplace. Attackers adapted methods that worked so well with email worms like the ILOVEYOU worm of 2000 to create a new kind of worm that could spread even faster over IM networks.
============================================
Gust MEES
Check out also my curation and my FREE course about it:
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
- http://www.scoop.it/t/securite-pc-et-internet?tag=BYOD
- http://www.scoop.it/t/21st-century-learning-and-teaching?tag=BYOD
============================================
Read more, a MUST: http://consumerization.trendmicro.com/dont-let-byod-become-byov-bring-your-own-viruses/
While mobile device management will always be in use in the enterprise, thankfully, a better option exists.
In fact, it seems the only group not excited about BYOD is IT – the ones who have to figure out how to keep sensitive corporate information safe. IT's consternation over BYOD is made worse by the fact that many think mobile device management (MDM) is the only tool available to contain the risks associated with BYOD, which is not the case.
MDM will always have a place in the enterprise because BYOD will simply never be the right approach for every employee. However, when it comes to BYOD implementations, MDM is not ideal. Thankfully, a better option exists. Mobile application management (MAM) presents an intriguing option for preparing for and avoiding the hazards of BYOD.
Read more, a MUST: http://www.scmarketscope.com/mdm-and-byod-a-square-peg-for-a-round-hole/article/260623/
The BYOD trend will make cyber security more complex Of the tips put forward by IDC, the first one is perhaps the most obvious and perhaps the reasons why the BYOD trend has caused so many headaches.
“The consensus is that BYOD is now a given. Whether you want it or not, employees will do your work on their own devices,” says Infosec commentator Stilgherrian.
“So your choice is whether to have a policy that acknowledges that and lays out the ground rules, or try to ban it and end up with an infestation of unknown and uncontrolled devices.”
However, as many enterprises are currently finding out, controlling and securing data on multiple devices is a lot easier said than done.
Read more, a MUST: http://technologyspectator.com.au/byod-security-commandments
A Toolkit to Support Federal Agencies Implementing Bring Your Own Device (BYOD) Programs
Product of the Digital Services Advisory Group and Federal Chief Information Officers Council
Read more: http://www.whitehouse.gov/digitalgov/bring-your-own-device
Si 34% d’entreprises interdisent l’usage de terminaux personnels, elle sont également 55% à appliquer des règles strictes pour encadrer l’accès aux documents professionnels depuis ces appareils.
nCircle is the leading provider of automated security and compliance auditing solutions.
Gust MEES: while using e-Learning, m-Learning and "Bring Your Own Device" (Hashtag on Twitter = #BYOD) we need to know the dangers, risks and ALSO that NO DEVICE is perfect! ANY device containing a computer, even a mini-computer is vulnerable! Mini-computer? YES, also a smartphone with what ever OS is vulnerable as it is more a computer than a phone!
Please check my FREE courses and curations here to get smart and don't forget "Forewarned is Forearmed"!
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
- http://gustmees.wordpress.com/category/get-smart-with-5-minutes-tutorials/
- http://gustmeesen.wordpress.com/2012/03/16/beginners-it-security-guide/
- http://www.scoop.it/t/ict-security-tools
- http://www.scoop.it/t/securite-pc-et-internet
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
===> Be aware of the malware!!! <===
Read more, a MUST: http://www.ncircle.com/index.php?s=resources_surveys_Mobile-Security-Policy-2012
A new report from the Consortium for School Networking (CoSN), titled “Safe & Secure?
“Apps and mobile devices are being utilized more and more in education, forcing schools to reexamine their mobile device policies,” said CoSN CEO Keith Krueger. “These continuous advancements are creating an unprecedented set of safety and security challenges for school leaders, so it’s imperative that leaders are prepared and have at their fingertips a set of technical solutions to prevent data breaches and protect personal devices.”
Gust MEES: read also my FREE courses here
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
- http://gustmees.wordpress.com/category/get-smart-with-5-minutes-tutorials/
Read more: http://www.eschoolnews.com/2012/09/10/cosn-examines-byod-safety-and-security/
|
Businesses today are embracing BYOD- 75% of businesses let employees use their own devices to access the network. What threats are lurking behind this mobile revolution?
Is BYOD a blessing or a curse?, asks Emma Byrne (@SciWriBy) Enthusiasts of the Bring Your Own Device (BYOD) trend are quick to point out the benefits for tomorrow’s business. Meanwhile, detractors warn of the increased costs and security headaches.
Gust MEES's insight:
People may think their shiny new smartphones and tablets are safe from hackers and malicious software, but that isn't the case, Internet security
Gust MEES's insight:
===> BEWARE of the MALWARE!!! <===
Bring Your Own Device policies could be a good way for schools to digitalize the teaching environment without breaking the bank.
Yet, before opening up their networks to devices students bring from home, it is important that schools take steps to ensure ===> that it’s done safely and effectively. <=== Jonathan P. Costa, Sr. – writing for EDTECH – details what the schools need to do to accomplish that goal.
Gust MEES's insight:
A MUST read!
Check also:
- - https://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
Spoofing, banking attacks, authentication flaws, and more top the list of 2012's biggest mobile security headaches
Gust MEES's insight:
Check out also my #curation here:
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free?tag=Mobile-Security
Mobile Device Security: What Senior Managers Should Know
This article provides clear, practical guidance on how you can make sure mobile ===> devices are a benefit rather than a risk for your organization. <===
Read more, a MUST:
The Bring-Your-Own-Device trend makes sense. It’s cost-effective and lets students use the device they already know and love. While it may present some problems for your school or district’s IT department, it’s a great start to bringing in web 2.0 tools and apps to the classroom.
BYOD is getting adopted at a rapid clip these days. But thanks to a new infographic, we have a closer look at the BYOD trend. Entarasys outlines 5 key facts (on the left side of the infographic, the right side is more business-y) that teachers, students, and school administrators should know about.
Read more, a MUST: http://edudemic.com/2012/10/5-things-to-know-about-the-byod-trend/
Does your child bring a handheld device to school to access the Internet?
Read more: http://info.uknowkids.com/blog/bid/234136/BYOD-Bring-Your-Own-Device-School-Policy

Erica Cruz's curator insight,
October 20, 2015 2:45 PM
This article made me think about what are my school policies and guideline for safe use of a mobile device at school.
Bring your own device (BYOD) is gaining more and more ground within enterprises, as employees are increasingly using their personal smartphones and tablets to check email, edit documents and do other work.
Read more, a MUST:
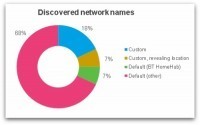
Do you always turn WiFi off on your smartphone before leaving the house or work? You might think there's no harm in having WiFi turned on but not connected to a network, but that's not necessarily the case.
A wireless device goes through a discovery process in which it attempts to connect to an available wireless network. This may either be ‘passive’ - listening for networks which are broadcasting themselves - or ‘active’ - sending out probe request packets in search of a network to connect to.
Most devices use both passive and active discovery in an attempt to connect to known/preferred networks. So it's very likely that your smartphone is broadcasting the names (SSIDs) of your favourite networks for anyone to see.
===> An ‘evil twin’ attack could even accomplish this without needing any knowledge of your WiFi password - very damaging for all of those who use mobile banking for instance! <===
Gust MEES: a MUST READ for anyone using m-Learning + "BYOD" and also any smartphone user...
OpenDNS and the Ponemon Institute teamed up to create a unique infographic that provides statistics on one of the most concerning topics in the industry.
Gust MEES
Please check my FREE courses and curations here to get smart and don't forget "Forewarned is Forearmed"!
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
- http://gustmees.wordpress.com/category/get-smart-with-5-minutes-tutorials/
- http://gustmeesen.wordpress.com/2012/03/16/beginners-it-security-guide/
- http://www.scoop.it/t/ict-security-tools
- http://www.scoop.it/t/securite-pc-et-internet
- http://www.scoop.it/t/apps-for-any-use-mostly-for-education-and-free
===> Be aware of the malware!!! <===
Read more: http://www.scmagazine.com/mobile-security-stats/slideshow/805/#0
“BYOD” Bring Your own Device. A great idea that can easily turn messy.
Biztech has introduced the BYOD: The Good, the Bad and the Ugly infographic asking you to answer 6 easy but important questions before you launch into a BYOD situation.
If your company is considering allowing employees to bring their own devices to work, make sure you have a game plan in place. BYOD has freed up many enterprises from the responsibility of exclusively purchasing and maintaining computing devices, such as notebooks, tablets and smartphones, but companies still need to have policies set in place to make things work. BizTech magazine has put together an infographic that highlights six core questions every company should consider before moving forward with BYOD:
- Who buys the devices?
Gust MEES: please read also my FREE course here
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
Read more: http://www.coolinfographics.com/blog/2012/9/10/byod-the-good-the-bad-and-the-ugly.html
|






![Why You Should Care About Mobile Security [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)













![5 Things To Know About The BYOD Trend [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/jhlRQ5qqQMbKeahkNbC1xjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








Learn more:
- http://www.scoop.it/t/securite-pc-et-internet?q=BYOD
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/